Sniffing I2C Traffic With a Bus Pirate
In a previous post I wrote about how to connect up an I2C EEPROM to the Raspberry Pi and read and write to it. In this post, I'll show how the Bus Pirate can be used to sniff the I2C traffic. It turns out, there's a gotcha that gave me some head scratching.
As far as wiring and software setup, it's the exact same from the previous post with the exception of adding on the Bus Pirate connections to the SDA and SCLK pins, along with a ground. Also, I swapped out the Bus Pirate from being my Serial to USB converter in order to be the I2C sniffer and used a MCP2200 Breakout Module instead.
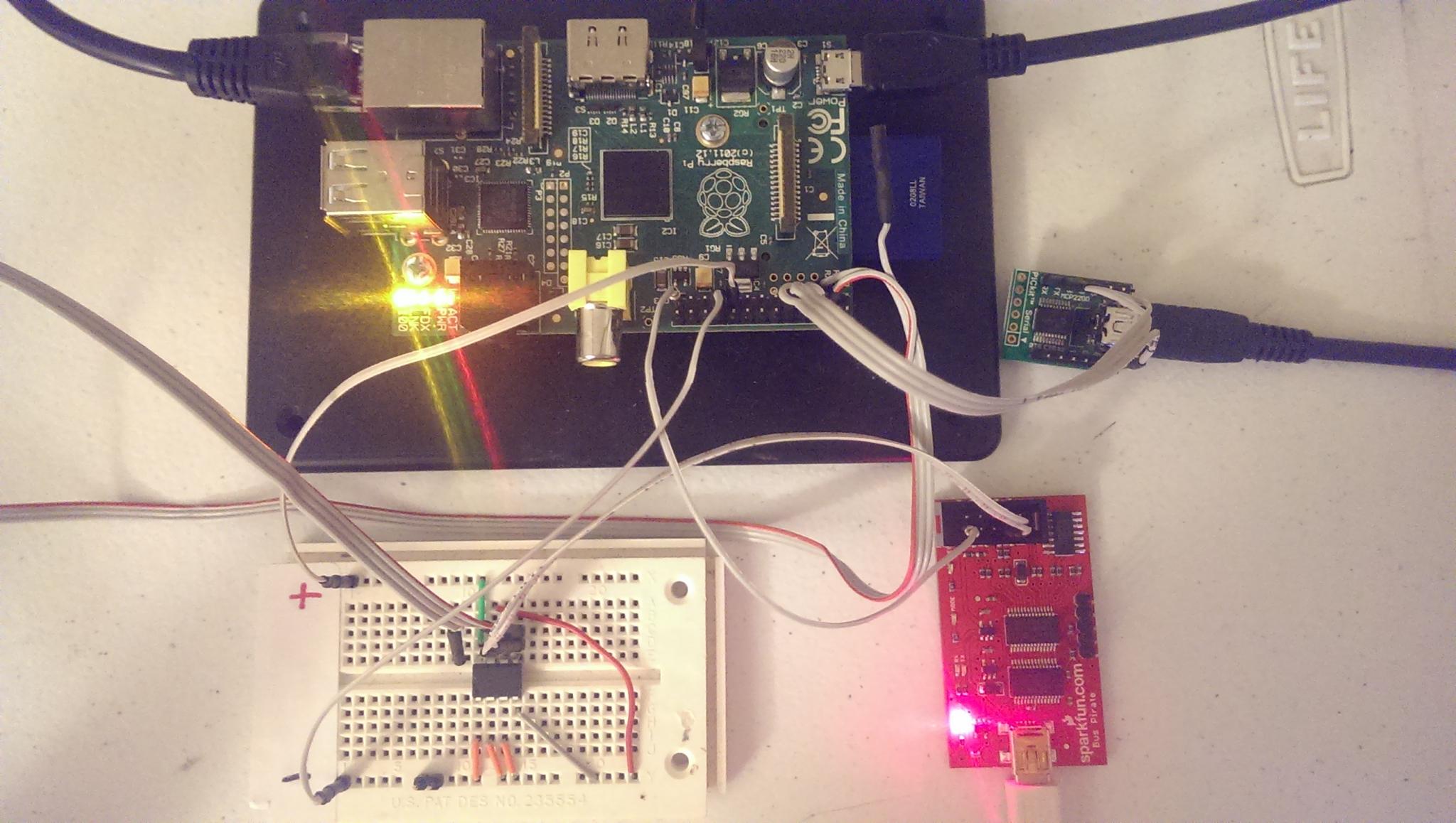
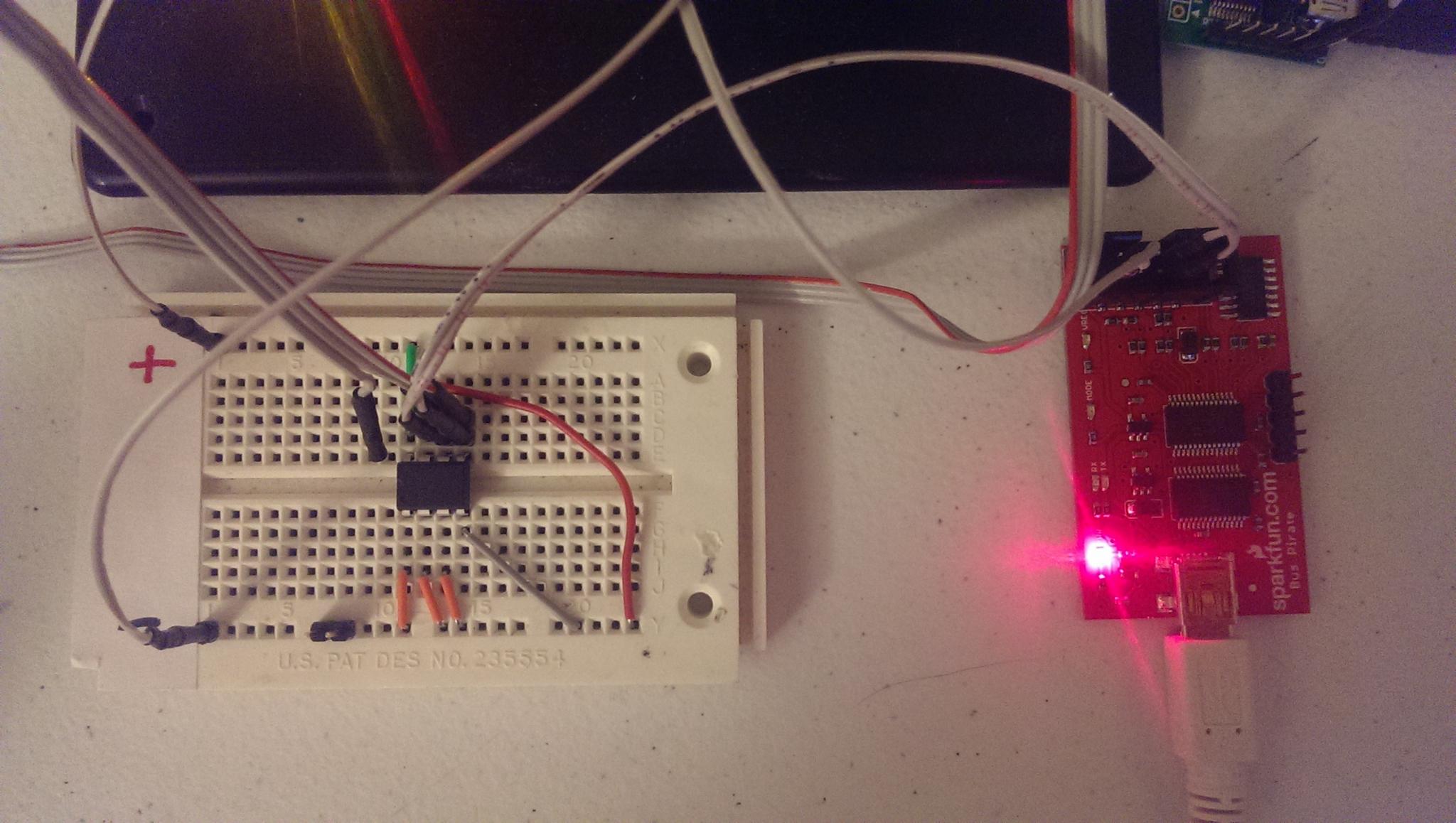
Now, with everything connected up, we can put the Bus Pirate in I2C sniffer mode. The last command is a macro to put it in sniffer mode.
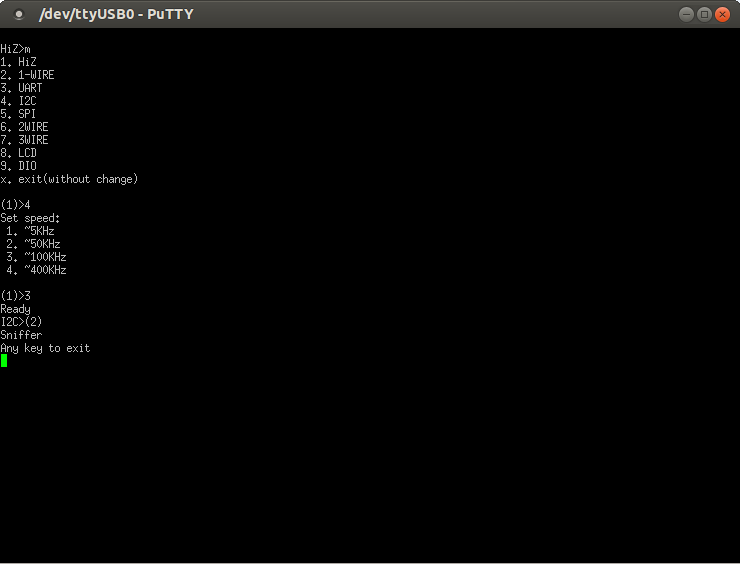
Now, jump over to the Raspberry Pi. Here's the gotcha. By default, the baudrate on the RaspBerry Pi I2C bus is at 100KHz. Even though the Bus Pirate claims to support this in the menu above, it really doesn't. It will surely read the traffic, but it will make no sense. Turns out, we can change the baudrate on the Raspberry Pi with a simple parameter to the i2c_bcm2708 module shown below to something like 32KHz. Just unload the module and re-insert it. You can also verify the baudrate with a file in sysfs. Then, write something to the EEPROM.
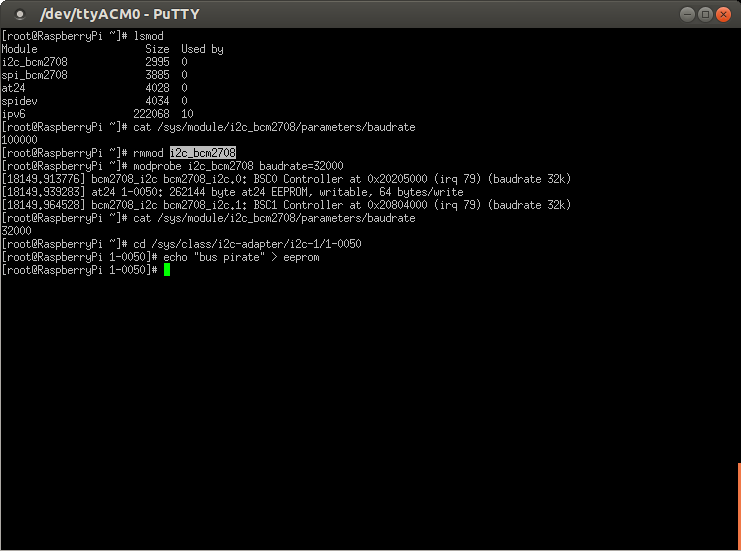
As we can see, we get a clean dump of the I2C communications. You can make out "bus pirate" in hex in the output.
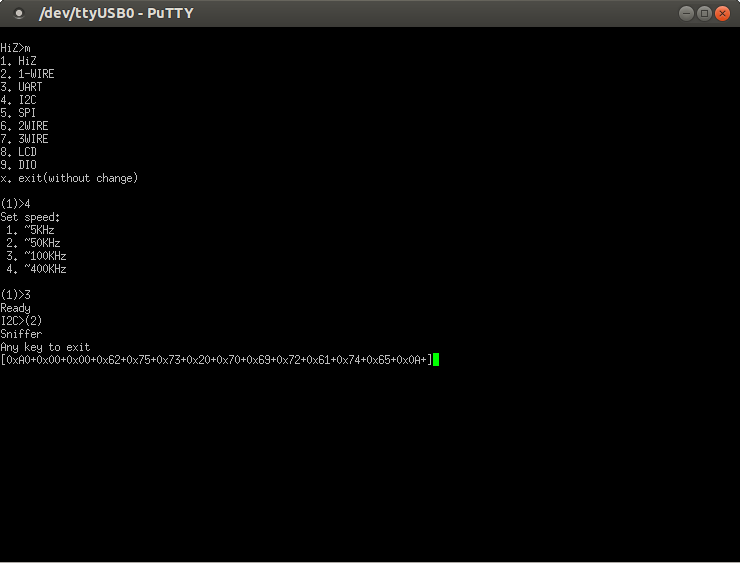
I won't show doing an actual read of a couple bytes because the at24 driver actually does a full page read even if you only want a couple bytes. So, it dumps a lot of traffic.
While this is no replacement for a real logic analyzer or an oscilloscope, it sure is an easy way to monitor communications quickly and easily. Oh yea, and the Bus Pirate can function as an oscilliscope as well, but I don't trust it very much.

1 Comment